Security Strategies for Data Center Interconnect
Data security and privacy concerns continue to intensify along with the risks and costs of data breaches, leading many network operators to seek new security strategies and tools. One tool attracting particular interest among cloud service providers and data center operators is in-flight data encryption for data center interconnect (DCI) links. Advances in encryption technologies, systems, and solutions are now making it possible for all data traversing DCI links to be encrypted simply and cost-effectively, and with virtually no impact on DCI scalability and performance.
DCI Security Drivers
Data security and privacy are among the top concerns for enterprise information technology (IT) executives. New security threats and attack vectors appear frequently, requiring constant attention to monitoring, defense, and mitigation of attack impacts. The financial cost of a security breach can be substantial, especially when customer data is exposed. Lost customer trust and reputational damage can lead to revenue loss. Financial penalties imposed by regulatory agencies or civil court judgments can materially affect profitability.
In this environment, IT managers and network operators recognize that security strategies must be comprehensive. Gone are the days of hoping that perimeter security, including firewalls and intrusion detection systems, will be sufficient to protect the networks behind them. The new assumption must be that every part of a network is vulnerable and any data traversing a network could be seen or captured by an attacker.
Even fiber-optic networks, sometimes assumed (wrongly) to be inherently secure, are vulnerable to fiber tapping, which enables data to be captured and copied without alteration as it is transmitted over a fiber. A few high-profile incidents of fiber tapping, including the revelation that Google’s and Yahoo’s private backbones had been tapped, have alerted network operators to this issue, adding to the already growing interest in the use of in-flight data encryption for data traversing networks.
Demand for in-flight data encryption was initially strongest among selected enterprise verticals, including financial services and government, but it is now growing across a broad range of customers in every market. Of particular note: Hyperscale cloud service providers are increasingly enabling encryption across their massive DCI networks to meet customer expectations. As enterprises move more of their IT infrastructure and mission-critical applications to the cloud, they demand very high security from cloud services, which has led cloud service providers to become some of the fastest growing users of in-flight encryption for DCI.
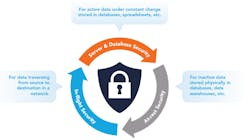
Of course, in-flight data encryption is no more of a security panacea than any other tool. It must be viewed as part of an overall security strategy that includes encryption of data in use and data at rest, as shown in Figure 1.
In-flight Encryption Options
In-flight encryption options are available at multiple layers of the protocol stack, but not all these approaches are created equal. As shown in Figure 2, encrypting at the application layer has the advantage of being truly end-to-end. But that advantage is far outweighed by the operational complexity of embedding encryption into every application and the performance challenges of software-based encryption. Internet Protocol security (IPsec) is widely used and accepted for internet-based virtual private networks (VPNs), but it suffers from high overhead and other disadvantages when applied to DCI. The better choices for DCI are encryption at lower layers, either Layer 1 encryption or media access control security (MACsec) at Layer 2.
MACsec is standards-based and widely accepted, like IPsec, but has inherently lower overhead. Hardware-based implementations of MACsec, delivering line-rate encryption with very low latency, are available from multiple component vendors. Because MACsec is well-established and aligned to Ethernet-based DCI requirements, it is the preferred choice for some hyperscale cloud providers.
Layer 1 (L1) encryption is an emerging choice that matches the low-latency and high-performance characteristics of MACsec and provides incremental benefits. Encryption protocol overhead measured at the Ethernet layer is eliminated completely with L1 encryption because it is part of the lower layer frame. L1 encryption also supports non-Ethernet traffic (most notably Fibre Channel for DCI).
Considering all the options, MACsec and L1 encryption are both good choices for DCI, capable of providing similar benefits and performance.
Built-in Encryption Support: Cost-effective and Simple
In-flight encryption is not only gaining momentum due to customer demands. It is also much more cost-effective and simple to implement than it was in the past. Hardware support for encryption is increasingly built into DCI systems and enabled through simple software licensing. Powerful hardware-based encryption engines are now integrated into other components in the DCI system, including the application-specific integrated circuits (ASICs) that provide digital signal processing (DSP) to drive high-capacity WDM-based optical engines.
Whether these optical engines reside in a purpose-built DCI appliance or on a WDM transponder card in a modular system, they can protect 100% of the data traversing the DCI network with no need for incremental hardware to be purchased, deployed, and managed.
Delivering a Complete Approach for In-flight Encryption
A complete approach for in-flight encryption includes several components, each of which should conform to strong standards and best practices to ensure a high security:
- Before two DCI endpoint devices can exchange keys and begin encrypting data, each device must be authenticated. Best practices used in other IT applications, including X.509 certificates and public key infrastructure (PKI), can be applied equally well for DCI devices.
- The data encryption should conform to the strongest standard, AES-256-GCM (Advanced Encryption Standard cipher with 256-bit keys and Galois/Counter Mode of operation), and the data encryption keys should be different from the keys used for device authentication.
- Authenticated DCI devices must create a shared key for secure data exchange using a key exchange protocol. The best practice for efficient exchange of AES-256 keys uses the elliptic curve Diffie-Hellman (ECDH) protocol with a 521-bit elliptical curve key size.
- To further strengthen security, data encryption keys should be changed regularly, ideally as frequently as minutes or even seconds, without any interruption to the data flow. Such hitless fast key rotation limits the amount of data that can be compromised in the unlikely event that any single key is discovered or cracked.
- Access to the DCI devices themselves should be secured to ensure that the encryption hardware and keys cannot be compromised by unauthorized users. The Federal Information Processing Standard Publication (FIPS PUB) 140-2 standard defines varying levels of device security that may be required by some DCI operators.
- Last but not least, while encryption can seem inherently complicated, a good in-flight security scheme should be designed to be as simple as possible for initial implementation and ongoing management.
DCI Encryption Use Cases
As noted above, a wide variety of customers are adopting in-flight encryption for DCI. Three examples highlight the diversity of applications.
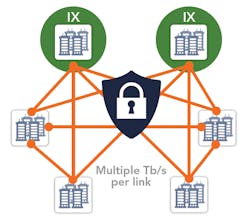
Secure Metro Cloud – Hyperscale cloud service providers have extended their networks to metro areas around the world. In each metro area, they typically have multiple data centers, all interconnected with each other and to local internet exchange (IX) facilities. These metro cloud networks are increasingly being secured with in-flight data encryption on every DCI link, as shown in Figure 3.
Financial Services – Financial services firms often rely on distributed data centers to ensure business continuity and highly available trading and transaction services. The DCI links between these data centers must deliver very high performance, with particular attention to low latency, while simultaneously ensuring high security. Line-rate encryption built into DCI systems can satisfy these requirements.
Health Care – Health care providers operating networks of hospitals and clinical facilities use optical DCI for the efficient sharing of patient medical records and images across the network. Given customer privacy expectations and strong regulations, such as the Health Insurance Portability and Accountability Act (HIPAA), patient data must be treated as highly sensitive and secured at all times. In-flight data encryption on all DCI traffic can complement other patient data protection methods and provide an additional measure of protection.
Looking Ahead
With growing demand for DCI encryption and cost-effective approaches emerging to meet that demand, in-flight encryption looks likely to become much more prevalent in DCI applications. Compact DCI systems offering MACsec and L1 encryption as part of a complete security strategy already enable leading customers to protect 100% of the data on their DCI networks, for applications as diverse as cloud services, financial services, and health care. As more customers adopt this highly scalable approach, in-flight encryption looks likely to become a standard expectation for all DCI links in the foreseeable future.
Jay Gill is principal product marketing manager at Infinera.