Protection and restoration for the new carrier-network model
"Just-in-time" carrier networks can use a mesh topology to offer a range of protection services for data traffic based on metropolitan customers' needs.
Protection technology has evolved in fiber-optic networks to the current practice of using Synchronous Optical Network/Synchronous Digital Hierarchy (SONET/SDH) rings with several restoration options. Emerging technologies that support coarse bandwidth protection for intercity optical routes will become available from vendors such as Ciena Corp. (Lightera), Cisco Systems (Monterey Networks), and Sycamore Networks. These systems will provide provisioning and protection for STS-1 or OC-N bandwidth increments.
Metropolitan interoffice networks will continue to rely on SONET/SDH rings and traditional protection schemes, however. These systems have to provide protection for services used in the residential, small-business, enterprise, and Internet service provider (ISP) markets. The bandwidth for these services typically ranges from 56 kbits/sec to OC-3 (155 Mbits/sec). There is an alternative: a new service-oriented protection model that takes advantage of the mesh topology frequently used in emerging carriers' networks. This new approach meets the needs of metropolitan carriers' residential and business data-service customers.
Today, protection and restoration in the fiber world is based on the widespread use of SONET/SDH ring technology. SONET/SDH rings typically provide path protection and restoration using either a unidirectional path-switched ring (UPSR) or a bidirectional line-switched ring (BLSR). Both technologies can support two or four fiber modes. Simply stated, in a unidirectional ring, the transmitted and received traffic travels in the same direction around the ring. A bidirectional ring, on the other hand, sends transmitted and received traffic through the same nodes but in opposite directions.
A UPSR works by having the transmitting end of a signal send the identical signal over two diversely routed paths to the destination. The destination node receives the two signals and then determines which signal is the best quality.
In a BLSR, a single signal is sent in one direction around the ring. In the event of a link failure, traffic is looped back in the SONET/SDH element adjacent to the failure. Protection bandwidth must be reserved for this potential failure, but it can also be used for low-priority pre-emptable traffic.
Current SONET/SDH protection implementations seek to restore traffic within 50 msec in order to restore service under the threshold established to trigger downstream carrier group alarms. To put this amount of time in perspective, a blink of the eye takes about 100 msec. Any new protection and restoration method used with a legacy circuit infrastructure must continue to meet this 50-msec goal.
What's involved in achieving this protection objective? First, the fiber outage is detected. SONET/SDH standards allow up to 10 msec to detect either the loss of light degraded line or missing sonet/ sdh frames. Next, the network elements (NEs) are notified of the outage; a message is sent to each network element--the length of the message and the internal processing required factor into the time allotted. The speed of light, 0.5 msec per 100 km for each link, is also taken into account. Finally, the NEs must re-map services to the protection spans, filling them up--at the speed of light.
Physics controls some elements of this process, such as the speed of light and the link-outage detection. Equipment manufacturers have influence on others, for example, the re-mapping of services to the protection spans.
The UPSR is the fastest protection-switching implementation because the traffic is redundantly presented to the recipient device all the time. The protection switching is relegated to a local switch that is extremely fast.
More processing is required for path switching and the receiver must have split copies and the intelligence to accomplish the task. Line switching, however, is more prevalent because it is simple. In the event of a failure, the NE locally switches the traffic.
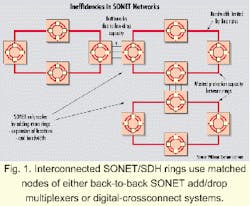
The issue with both the UPSR and BLSR protection schemes is that half of the fiber in each ring is generally not used. This fiber capacity is in standby mode waiting for a "protection event" to occur.The cost of this unused capacity is further exacerbated because many met ropolitan carriers have multiple SONET/SDH rings in place in a given city (see Fig. 1). With today's explosive bandwidth demand, the fixed line rate of a SONET/SDH ring is often easily exceeded when one or two customers order OC-N services, resulting in the need for even more SONET/SDH rings and commensurate protection bandwidth.
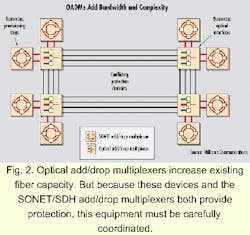
The use of optical add/drop multiplexers (OADMs) that convert standard SONET/SDH 1310 nm to dense wavelength-division multiplexing (DWDM) via transponders can preserve fiber capacity. In this scenario, the cost of the OADM equipment replaces the cost of using additional fiber. The OADMs also help carriers avoid the "time to provision" consideration when new fiber has to be pulled through an existing conduit or worse if new conduits must be installed. The use of an OADM in combination with service aggregation NEs such as SONET/SDH add/drop multiplexers (ADMs) or Asynchronous Transfer Mode (ATM) switches is an approach that is gaining in popularity (see Fig. 2). Many OADMs will offer protection services as a value-add.Since both the OADMs and the attached NEs provide protection, this equipment must be carefully coordinated, or a situation known as "thrashing" may occur. Thrashing occurs when two or more concatenated communication systems provide self-healing mechanisms for failures. A single network failure can trigger these mechanisms. The self-healing action of one device can terminate the mechanism in another device. Thus, the systems could go back and forth between the primary configuration and the protected state several times before the network stabilizes.
Thus, the OADMs should provide protection well below the 10-msec threshold of SONET/SDH rings to ensure that SONET/SDH would not initiate protection before the OADM restores the span. Most OADMs implement protection using 1+1 automatic protection switching (APS) built upon two DWDM channels between SONET/SDH ADM spans, ATM switches, or routers. The current street price of an OC-48 (2.5-Gbit/sec) DWDM transponder ranges from $20,000 to $30,000 each. Four transponders are needed for the APS implementation; therefore, the cost of this approach can range from $80,000 to $120,000 per span.
The high-bandwidth customers are often ISPs or large enterprises operating data-only environments. Many of these customers ask their respective carriers to provide high-bandwidth services without SONET/SDH quality protection at lower prices. This class of customer will often point out that their own ATM switches or routers have the ability to re-route data traffic upon link failures. Even if it takes 10 or more seconds to restore service, data applications can tolerate such an outage without significant degradation.
The new generation of integrated service carriers has a fundamentally different business model than the regional Bell operating companies (RBOCs) and the incumbent local-exchange carriers (ILECs). The RBOCs built metropolitan central offices about 18,000 ft apart in the first half of the century based on copper transmission limitations at the time. This distance provides fixed locations to connect with existing conduit. Ring topologies can work well in this environment.
In contrast, the new carriers build their networks as they acquire customers and therefore need more topological freedom. For these carriers, networks can start as a spur, or spoke, or access link, and incrementally develop into a ring and then a mesh topology without service disruptions due to hardware or software upgrades. The ILECs must adhere to this business model as they compete for out-of-region business.
This new business model requires a different approach to protection and restoration. Unlike the "one size fits all" model of line-switched SONET/SDH protection, the new approach features a service orientation, which allows carriers to offer a variety of protection services based on customers' needs.
Legacy equipment can still be provisioned to support traditional SONET/SDH less than 50-msec restoration performance, allowing carriers to install equipment midstream in an existing infrastructure without service disruption. On the other end of the spectrum, carriers can offer data services without protection, assuming that another device or network ensures service availability.
Carriers can also sell low-cost pre-emptive bandwidth services that use protection bandwidth and are not available when a failure occurs. A pre-emptive service is very useful when applied to store-and-forward applications such as e-mail. Similarly, packet, ATM, and frame-relay services could have "intermediate protection" that allows a reduction in the committed information rate during a protection event.
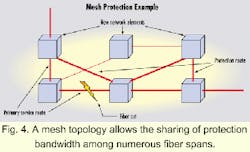
These types of services are very attractive if they can be provided at a lower cost than the current mode of operation using SONET/SDH rings--carriers must still make the requisite margins. To accomplish this, carriers need to build lower-cost infrastructures that use protection bandwidth more efficiently.The key to achieving a low-cost infrastructure is to provide protection and restoration in a mesh-topology network. This network, by definition, is more scalable than a SONET/SDH ring environment to allow fiber spans located throughout the infrastructure to provide protection for individual failures in various links (see Fig. 4). Localized protection is faster and more efficient. It does not make sense to protect an outage between Los Angeles and Orange County with bandwidth re-routed across the country through New York.
Studies show that mesh topologies save about 30% of the total network bandwidth. One such study undertaken and published by ATT Research indicated a 35% reduction in network cost when an ATM-centric infrastructure was used versus a traditional circuit-switched SONET/SDH network. The mesh topology and the use of ATM in place of digital-crossconnect traffic grooming contributed to the lower total network cost, according to the ATT Research report.1
Mesh topology better supports the "just-in-time" business model in which carriers build networks as they acquire customers. The topology allows carriers to install NEs where and when needed. Mesh networks also grow in bandwidth capacity as nodes and spans are added.
SONET/SDH rings, by comparison, have fixed line-rate bandwidth, meaning that bandwidth is spread across the ADMs. As carriers add this equipment, it reduces the average bandwidth per ADM. Moreover, because the line rate of the ring is constant, adding spans in the network does not increase bandwidth.
A mesh-topology network combined with a service-orientation approach to protection and restoration offers a more efficient use of existing fiber and bandwidth. It also lowers equipment costs by reducing the number of SONET/SDH ADMs and reduces the total cost of the network. Finally, it will allow carriers to offer a range of protection services that meet residential and business customers' data needs in metropolitan areas.
- IEEE Communications magazine, "Future Transport Network Architectures," R. Doverspike, S. Phillips, J.R. Westbrook, ATT Labs-Research, August 1999.
Bill Mitchell is the vice president of marketing at Astral Point Communications (Chelmsford, MA) www.astralpoint.com